The basic principle of our technology consists in introducing at different levels of the visible marking (visible image, logo, number, etc.) of additional, hidden (secret) information. That additional hidden (secret)information is different and specific not only for each level where it is embedded, but also for each individual object of protection and is generated and provided by independent sources (manufacturer, control authority, etc.) The link and relationship between the visible image (information, number, logo, etc.) and the embedded (hidden, secret) information for any specific level is recorded in a database on a writ only media CD-ROM/DVD-R to ensure protection against unauthorized and/or undesired modifications or corrections.
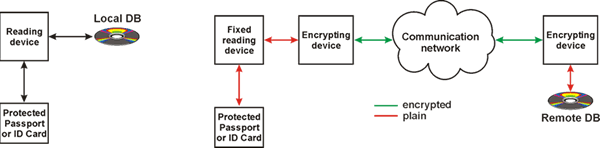
In view of the independence of the different levels of protection, access to the personalization procedure will have only the respective authorities, responsible for the provision and generation of the hidden visual information (encoded) for the respective level.
In such a way we obtain an independent protection within the protection and if by chance an information at one level is falsified or forged, as a result of leak of security information or corruption within one organization, the encrypted information for the other levels remains valid and safe. Thus if somebody had the intention to brake the security codes and reproduce the original security markings, he would need also to replace the original records in the databases for each level of protection. As a result the possibility of fraud, forgery and reproduction of the original unique security marking is very much limited.

 Home
Home
 About us
About us
 Services
Services
 Managment
Managment
 Technologies
Technologies
 Contacts
Contacts